3GPP 5G Security
August 6, 2018
By Anand R. Prasad, Alf Zugenmaier, Adrian Escott and Mirko Cano Soveri
In December 2017, the Non-Standalone (aka. NSA) specifications for 5G new radio (NR) were approved, followed in June 2018, by the Standalone specifications – completing the radio part of 5G Phase 1 (3GPP Release 15). The 3GPP Security Working Group (SA3) has been involved from the outset of the work. In this article we briefly introduce security for both Non-Standalone [1] and the Standalone NR 5G system [2].
The 5G system is an evolution of the 4G mobile communication systems. Accordingly, the 5G security architecture is designed to integrate 4G equivalent security. In addition, the reassessment of other security threats such as attacks on radio interfaces, signalling plane, user plane, masquerading, privacy, replay, bidding down, man-in-the-middle and inter-operator security issues have also been taken in to account for 5G and will lead to further security enhancements. This article gives an overview of 5G Phase 1 security as described in Release 15 specifications [1,2].
A detailed discussion of 5G Phase 1 security is also available in [3].
The article starts with a description of Non-Standalone security followed by the laying out of the underlying trust models in the 5G system, considering roaming and non-roaming cases. In the final section key 5G Phase 1 security enhancments - compared to 4G - are discussed.
Non-Standalone NR Security
The first step standardized by 3GPP towards complete 5G coverage was Non-Standalone NR, also known as E-UTRA-NR Dual Connectivity (EN-DC) or Architecture ‘Option 3’ [1]. The key feature of Non-Standalone is the ability to utilize existing LTE and EPC infrastructure, thus making new 5G-based radio technology available without network replacement. EN-DC uses LTE as the master radio access technology, while the new radio access technology (i.e. NR) serves as secondary radio access technology with User Equipments (UEs) connected to both radios. Except for capability negotiation, security procedures for EN-DC basically follow the specifications for dual connectivity security for 4G.
A Master eNB (MeNB) checks whether the UE has 5G NR capabilities to access the Secondary gNB (SgNB), i.e. 5G base-station, and the access rights to SgNB. The Capability and access rights check ensures that the standard is forward compatible since UEs with different capabilities, including security capabilities, can join the network.
The MeNB derives and sends the key to be used by the SgNB for secure communication over NR; the UE also derives the same key. Unlike dual connectivity in 4G networks, Radio Resource Control (RRC) messages can be exchanged between the UE and SgNB, thus keys used for integrity and confidentiality protection of RRC messages as well as User Plane (UP) data are derived. Although integrity protection for UP data is supported in 5G network, it will not be used in EN-DC case. Use of confidentiality protection is optional for both UP and RRC.
Evolution of the trust model
Moving on from the Non-Standalone deployment, in a Standalone 5G system, the trust model has evolved. Trust within the network is considered as decreasing the further one moves from the core. This has impact on decisions taken in 5G security design, thus we present the trust model in this section.
The trust model in the UE is reasonably simple: there are two trust domains, the tamper proof universal integrated circuit card (UICC) on which the the Universal Subscriber Identity Module (USIM) resides as trust anchor and the Mobile Equipment (ME). The ME and the USIM together form the UE.
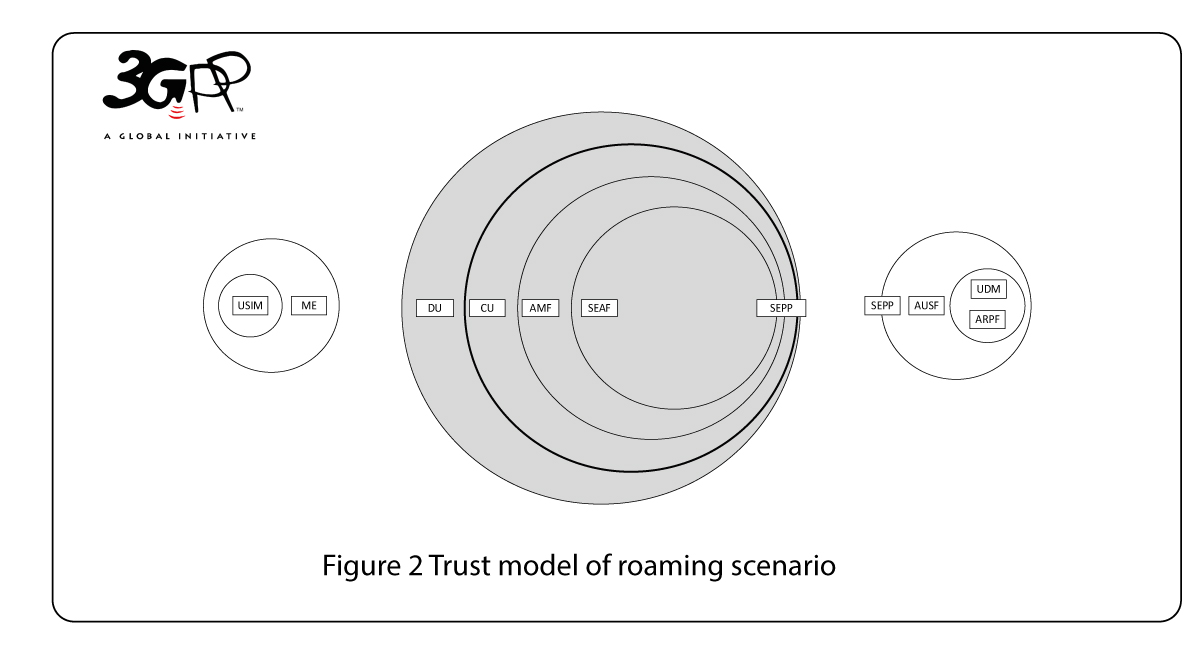
The network side trust model for roaming and non-roaming cases are shown in Figure 1 and 2 respectively, which shows the trust in mulitple layers, like in an onion.
The Radio Access Network (RAN) is separated into distributed units (DU) and central units (CU) – DU and CU together form gNB the 5G base-station. The DU does not have any access to customer communications as it may be deployed in unsupervised sites. The CU and Non-3GPP Inter Working Function (N3IWF – not shown in the figures), which terminates the Access Stratum (AS) security, will be deployed in sites with more restricted access.
In the core network the Access Management Function (AMF) serves as termination point for Non-Access Stratum (NAS) security. Currently, i.e. in the 3GPP 5G Phase 1 specification [2], the AMF is collocated with the SEcurity Anchor Function (SEAF) that holds the root key (known as anchor key) for the visited network. The security architecture is defined in a future proof fashion, as it allows separation of the security anchor from the mobility function that could be possible in a future evolution of the system architecture.
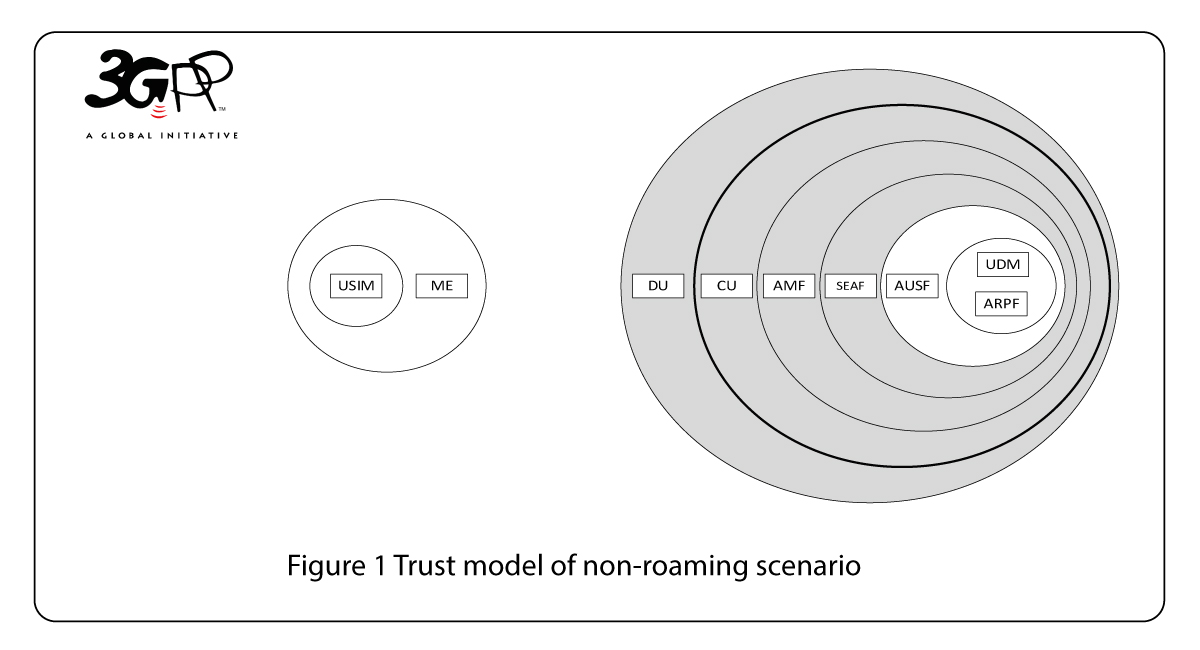 The AUthentication Function (AUSF) keeps a key for reuse, derived after authentication, in case of simultaneous registration of a UE in different access network technologies, i.e. 3GPP access networks and non-3GPP access networks such as IEEE 802.11 Wireless Local Area Network (WLAN). Authentication credential Repository and Processing Function (ARPF) keeps the authentication credentials. This is mirrored by the USIM on the side of the client, i.e. the UE side. The subscriber information is stored in the Unified Data Repository (UDR). The Unified Data Management (UDM) uses the subscription data stored in UDR and implements the application logic to perform various functionalities such as authentication credential generation, user identification, service and session continuity etc. Over the air interface, both active and passive attacks are considered on both control plane and user plane. Privacy has become increasingly important leading to permanent identifiers being kept secret over the air interface.
The AUthentication Function (AUSF) keeps a key for reuse, derived after authentication, in case of simultaneous registration of a UE in different access network technologies, i.e. 3GPP access networks and non-3GPP access networks such as IEEE 802.11 Wireless Local Area Network (WLAN). Authentication credential Repository and Processing Function (ARPF) keeps the authentication credentials. This is mirrored by the USIM on the side of the client, i.e. the UE side. The subscriber information is stored in the Unified Data Repository (UDR). The Unified Data Management (UDM) uses the subscription data stored in UDR and implements the application logic to perform various functionalities such as authentication credential generation, user identification, service and session continuity etc. Over the air interface, both active and passive attacks are considered on both control plane and user plane. Privacy has become increasingly important leading to permanent identifiers being kept secret over the air interface.
In the roaming architecture, the home and the visited network are connected through SEcurity Protection Proxy (SEPP) for the control plane of the internetwork interconnect. This enhancement is done in 5G because of the number of attacks coming to light recently such as key theft and re-routing attacks in SS7 [5] and network node impersonation and source address spoofing in signalling messages in DIAMETER [6] that exploited the trusted nature of the internetwork interconnect [7].
5G Phase 1 Security (Release 15)
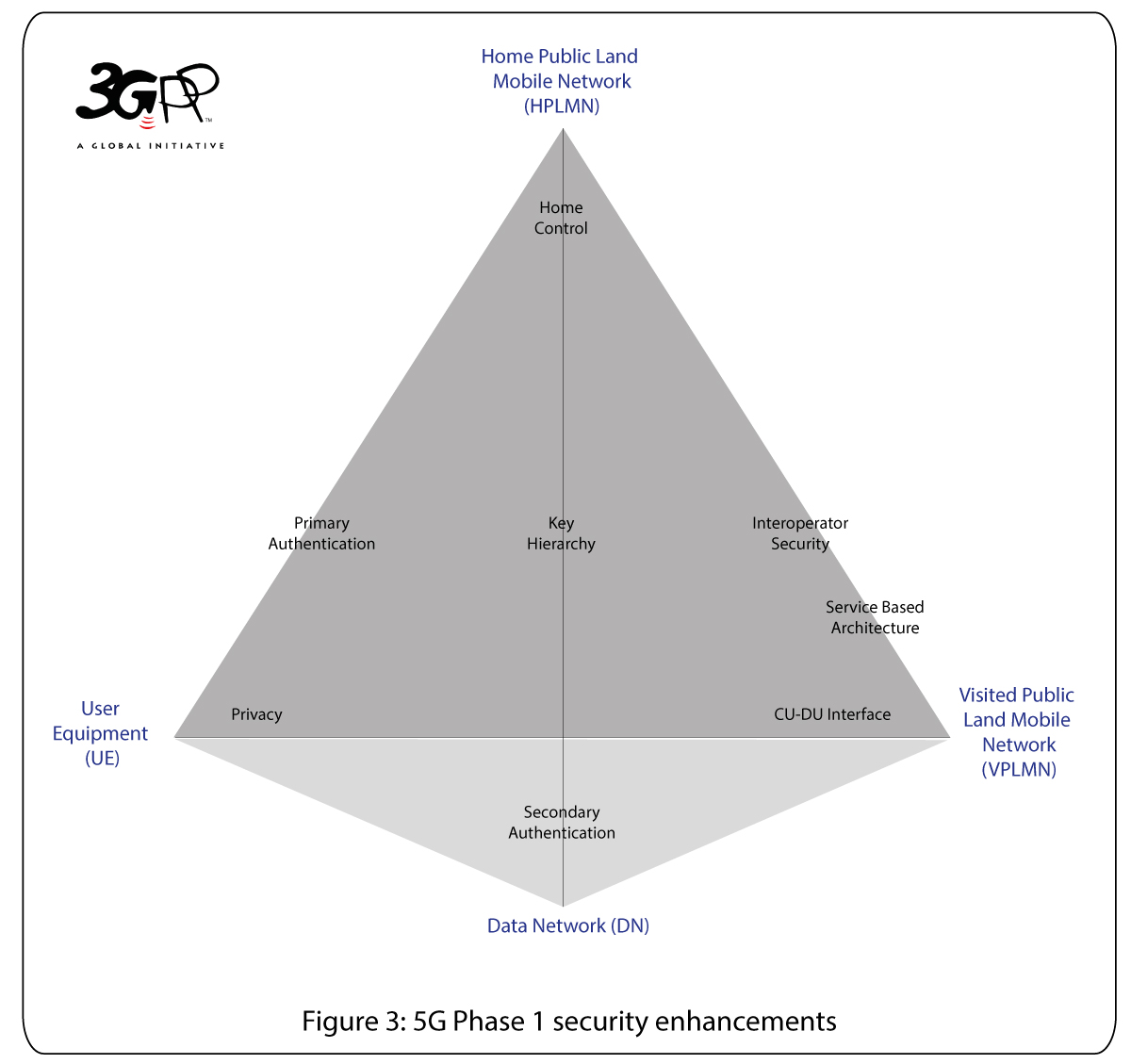
5G Phase 1 brings several enhancements to 4G LTE security, some of the key points are presented in this section [4]. Details of 5G Phase 1 security can be found in [2,3].
Primary authentication: Network and device mutual authentication in 5G is based on primary authentication. This is similar to 4G but there are a few differences. The authentication mechanism has in-built home control allowing the home operator to know whether the device is authenticated in a given network and to take final call of authentication. In 5G Phase 1 there are two mandatory authentication options: 5G Authentication and Key Agreement (5G-AKA) and Extensible Authentication Protocol (EAP)-AKA', i.e. EAP-AKA'. Optionally, other EAP based authentication mechanisms are also allowed in 5G - for specific cases such as private networks. Also, primary authentication is radio access technology independent, thus it can run over non-3GPP technology such as IEEE 802.11 WLANs.
Secondary authentication: Secondary authentication in 5G is meant for authentication with data networks outside the mobile operator domain. For this purpose, different EAP based authentication methods and associated credentials can be used. A similar service was possible in 4G as well, but now it is integrated in the 5G architecture.
Inter-operator security: Several security issues exist in the inter-operator interface arising from SS7 or Diameter [5,6] in the earlier generations of mobile communication systems. To counter these issues, 5G Phase 1 provides inter-operator security from the very beginning.
Privacy: Subscriber identity related issues have been know since 4G and earlier generations of mobile systems. In 5G a privacy solution is developed that protects the user's subscription permanent identifier against active attacks. A home network public key is used to provide subscriber identity privacy.
Service based architecture (SBA): The 5G core network is based on a service based architecture, which did not exist in 4G and earlier generations. Thus 5G also provides adequate security for SBA.
Central Unit (CU) - Distributed Unit (DU): In 5G the base-station is logically split in CU and DU with a interface between them. Security is provided for the CU-DU interface. This split was also possible in 4G, but in 5G it is part of the architecture that can support a number of deployment options (e.g. co-locataed CU-DU deployment is also possible). The DUs, which are deployed at the very edge of the network, don't have access to any user data when confidentiality protection is enabled. Even with the CU-DU split, the air interface security point in 5G remains the same as in 4G, namely in the radio access network.
Key hierarchy: The 5G hierarchy reflects the changes in the overall architecture and the trust model using the security principle of key separation. One main difference in 5G compared to 4G is the possibility for integrity protection of the user plane.
Mobility: Although mobility in 5G is similar to 4G, the difference in 5G is the assumption that the mobility anchor in the core network can be separated from the security anchor.
The Next Step
Non-Standalone and 5G Phase 1 Standalone architecture gave us a taste of the new generation of the mobile communication system. The main use case for 5G Phase 1 was mobile broadband. 5G Phase 2 will bring solutions for the Internet of Things (IoT), covering several scenarios in the form of massive Machine Type Communication (mMTC) and Ultra-Reliable and Low Latency Communications (URLLC). mMTC relates to very large number of devices transmitting a relatively low volume of non-delay-sensitive data and URLLC relates to services with stringent requirements for capabilities such as throughput, latency and availability.
For mMTC, very low data-rates going down to few bits per day, we will have to consider the extent of security (be it authentication, confidentiality, integrity or otherwise) that can be provided. Several IoT or Machine-to-Machine (M2M) services and devices fall under this category, examples are temperature sensors giving hourly updates, sensors on farm animals giving vital status couple of times a day etc. Such devices will also be resource constrained in terms of battery, computation and memory. For security the requirement will be to reduce the overhead of security related bits, e.g. for integrity, for every communication.
At the other end of the scale, URLLC devices will call for high data-rateswith potentially higher battery and computational resources; examples include cars, Industrial IoT (IIoT) devices like factory machinery and virtual or augmented reality (VR or AR) devices - used for gaming or real-time services. Providing higher data rates also means that throughput of security functions need to be considered to avoid processing delay.
References
[1] 3GPP TS 33.401, “Technical Specification Group Services and System Aspects: 3GPP System Architecture Evolution (SAE) Security architecture”.
[2] 3GPP TS 33.501, “Security architecture and procedures for 5G system”.
[3] Anand R. Prasad, Sivabalan Arumugam, Sheeba B and Alf Zugenmaier, “3GPP 5G Security”, Journal of ICT Standardization (River Publishers, Vol. 6, Iss. 1&2).
[4] “Key Points of 5G Security”, Opinion Pieces on Cyber Security (River Publishers)
[5] Tobias Engel. (December 2014). "SS7: Locate. Track. Manipulate" (Chaos Computer Club Berlin)
[6] GSMA RIFS: "Diameter Roaming Security - Proposed Permanent Reference Document".
[7] 3GPP TR 33.899, “Study on the security aspects of the next generation system”, Release 14, v 1.3.0, August 2017.

 3GPP News
3GPP News




